Table of Contents
Difference between SSH and SSL -SSH vs SSL
SSH (Secure Shell) and SSL/TLS (Secure Socket Layer/Transport Layer Security) are web security protocols that provide a secure encrypted connection over an unsecured network. Both utilize Asymmetric Cryptography and keep sensitive information safe when communications are made between browsers and servers.
In the previous years, files were transferred via FTP (File Transfer Protocol), whose primary function was to upload/download files on the internet or over LAN. The popularity of FTP attracted many cyber-attacks, like brute force attacks, sniffer attacks, etc. This led to the development of secure file transfer protocols like SFTP (used by SSH) and FTPS (which is used by SSL).
In the digital market, an insecure networks or systems can attract hackers and intruders to steal your data, sensitive information, applications, and files. Hence visitors and users demand web security, and that’s when SSH and SSL pop into the picture.
What is SSH?
Secure Shell is a cryptographic network protocol used to access and secure network devices and servers over an unsecured internet network. Where SSL is used to encrypt browser-server communication, SSH encrypts communication made between two computers. It helps in command execution by communicating with the operating shell of another system via remote access. It is also used for issuing remote commands as well as automated file transfers.
It ensures robust security and data integrity between the endpoints of the computer.
More about SSH:
- Its in-built username/password authentication system helps in simplifying the connection process. You can enable the same to establish a connection.
- For authenticating the connection process, it uses Port 22.
- For authenticating the remote system, it uses Public Key Cryptography, and thus remote computers can validate users.
- It protects against DNS spoofing, data manipulation, IP address spoofing, data spoofing during communications, etc.
- Previously created on UNIX operating systems, now SSH protocol is effortlessly executed on Windows too.
- Encryption and Authentication are the main functions of SSH.
How does SSH Work?
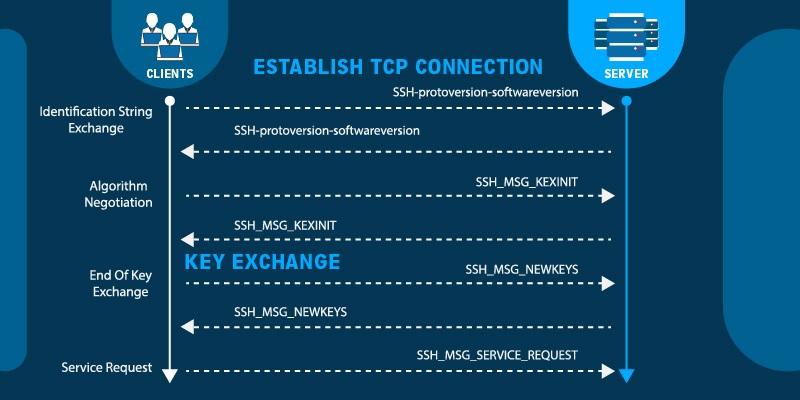
SSH protocol works on Public Key Cryptography, where the key pairs (public key & private key) are termed as SSH Keys. The public key is kept with the server, whereas the private key is with the client who is requesting remote access. The server will immediately confirm the private key and grant remote access to the client. To know in detail about the functioning of SSH.
A demonstration of an SSH handshake process is shown in the below image.
What do you understand about SSL/TLS?
SSL (Secure Socket Layer) certificate is a web security protocol that encrypts communications between clients (browsers) and servers, thus establishing a secure connection. In short, it ensures to keep data transmission secure, thus keeping intruders at a distance. All online businesses and e-commerce industries need an SSL certificate for giving a safe and secure environment for their users. They come in various types and validations.
Example: Wildcard SSL certificate secures the website’s primary domain and unlimited first-level sub-domains, providing ample encryption security.
Since SSL versions, SSL 2.0 and SSL 3.0 are outdated, TLS (Transport Layer Security), being the upgraded version of SSL, has replaced all its older versions. The term SSL is more popular, and hence it is frequently used as compared to TLS.
More about SSL:
- SSL/TLS runs on port 443 and is installed on the website.
- It shows trust symbols like a padlock in URL and HTTPS in the address bar.
- Different SSL certificates secure your site in different ways. I.e., a Domain SSL certificate secures the primary domain of the website whereas, a Multi-domain SSL certificate secures multiple domains and multiple subdomains (all levels) of the websites.
- They come with a site seal and secure your website with robust 256-bit encryption and 2048-bit key signatures.
- Their main functions are data encryption, authentication, and data integrity.
- They help in safeguarding online transactions and sensitive information transmitted on the internet.
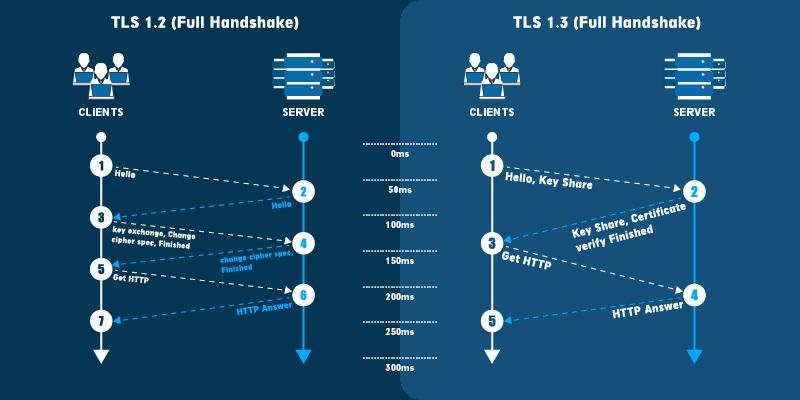
How does SSL/TLS Work?
SSL/TLS protocol works on Asymmetric Encryption, where Private Key and Public Key (cryptographic keys) are used in the process. The public key is available to the public, whereas the private key is securely stored in the webserver.
The private key decrypts the data which is encrypted by the public key.
Here, secure communication starts with a TLS handshake, where both the parties generate session keys for encrypting-decrypting communications. To know in detail about how the handshake process works.
A demonstration of an SSL handshake process is shown in the below image.
Similarities Between SSH and SSL/TLS:
- Both are security protocols used for securing connections.
- Both SSH and SSL use encryption technology to protect data transmission.
- The main task of both these security protocols is to establish a secure and reliable connection.
- Both these protocols are PKI (Public Key Infrastructure) based.
SSH vs. SSL:
Though SSH and SSL function in similar ways and have multiple similarities related to encryption aspects, authentication aspects, and maintaining data integrity, they have some eye-catching differences.
| SSH | SSL/TLS | |
| Abbreviation | Secure Shell | Secure Socket Layer |
| Port | It runs on port 22. | It runs on port 443. |
| Application | It encrypts all communication made between 2 computers and permits users to modify and control their servers. | It encrypts all communications made between the browser and server. |
| Industries which adopt | It is widely used by the Web (network) industry. | It is widely used by e-commerce, healthcare, banking, financial institutions, government companies, etc. |
| Tools for Authentication | It uses a public/private key or user-id/password pair for authentication. | It uses public/private key or x.509 digital signatures for authentication. |
| Task | SSH is used for executing commands on a server in a secure way. | SSL is used for encryption communications between browser and server.
|
| Works On | The working of SSH is based on network tunnels. | The working of SSL is based on SSL/TLS digital certificates. |
| Protocol | It is a remote protocol. | It is a security protocol. |
| Functioning | It is used to lessen the security threats for remote server login. | It is used to secure data-in-transit between browser and server. |
| Authentication Process | The authentication process includes server verification by browser, generation of a session key, and the client’s authentication. | The authentication process includes the exchange of a digital certificate. |
| Data Integrity | Data integrity is maintained by using algorithms like SHA, SHA-2, and SHA-256. | Data integrity is maintained by applying the message digest to the data before the transmission of data. |
| Certificate Authority | Since SSH depends mainly on key exchange, the organization need not go to a CA for issuance. It can create and distribute their key pairs. | Since SSL is a digital certificate, the organization needs to go to a CA for its issuance. |
| Protection | SSH is used for protection against DNS attacks, spoofing attacks on IP addresses, data manipulations, etc. | SSL is mainly used for protection against MIM (man-in-middle) attacks, brute force attacks, and identity theft. |
Wrapping Up:
Now that you are aware, though both these protocols have just a difference of a single alphabet, they are entirely different in their functionality and uses. They cannot compensate for each other. There may be a possibility that you may need to use both for security purposes.
But that possibility solely depends on your web security requirement. Though SSH is generally used as a tool for web developers and technicians, whereas SSL can be easily installed by users. With the rise in online threats, it is advisable to be vigilant and make the best use of these online security protocols.
Related Articles:
- What is Wildcard SSL Certificate?
- Cheap Wildcard SSL certificate
- Comodo PositiveSSL Wildcard vs. EssentialSSL Wildcard Certificate